Food chain service Zomato hacked. Yes, the company admitted the major security breach, which led 17 million user records (out of company’s 120 million users) stolen from its database, though the company claims that no payment information or credit card data has been stolen.
ALSO READ: After Cracking Into Netflix, OurMine Hits Marvel Accounts!
Zomato Hacked!
The breach has caused a disturbance and arose questions on company’s data security. According to the company, usernames and hashed passwords were stolen by attackers – the fact that the passwords were encrypted, which means it will be harder to break.

Zomato disclosed the attack in a blog post, where it mentioned that all payment data is stored in a highly secure PCI Data Security Standard (DSS) compliant vault and that no payment information or credit card data has been stolen. To be on a safer side, change your Zomato password right now and don’t forget to change it on others sites if have you used the same password.
ALSO READ: UberEATS Food Delivery Service Launched In India; Takes On Swiggy & Zomato!
More!
This is not the first time that Zomato has been targeted. In 2015, the company was hacked by Indian ethical hacker Anand Prakash, who addressed the security weakness to Zomato. On the flipside, HackRead reported that the stolen Zomato passwords are being sold on Dark Web marketplace.
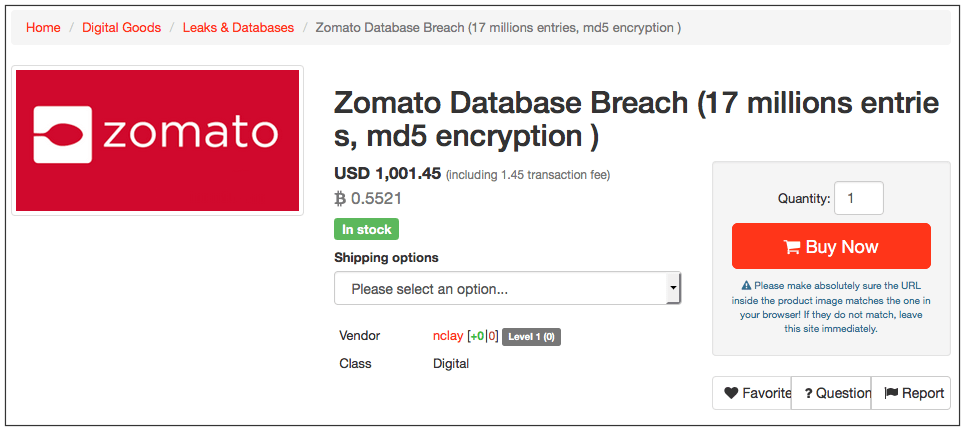
The database includes emails and password hashes of registered Zomato users while the price set for the whole package is USD 1,001.43 (BTC 0.5587). The seller also shared a trove of sample data to prove that the data is legit. Here’s a screenshot of the sample data publicly shared by “nclay.”

Zomato Said;
Over the next couple of days, we’ll be actively working to improve our security systems – we’ll be further enhancing security measures for all user information stored within our database, and will also add a layer of authorization for internal teams having access to this data to avoid any human breach.